If you’re wondering what a phishing scam or phishing email is, the answer starts with deception. These attacks are designed to trick you — or someone in your organisation — into handing over sensitive information or downloading something malicious.
The message might look like it’s from a trusted company, a colleague, or even a family member. But behind the scenes, it’s a scam designed to steal login credentials, financial data, or infect your systems with ransomware.
Phishing can strike via email, SMS, messaging apps, or even fake websites. As attackers adopt AI and more advanced techniques, these scams are becoming harder to detect — and far more damaging when they succeed.
What Is a Phishing Scam?
A phishing scam is a form of cyber-attack that tricks individuals into revealing personal or sensitive information, such as bank details or login credentials. Attackers often disguise themselves as reputable organisations using email, SMS, WhatsApp, or hijacked websites.
These scams usually contain malicious links or attachments. Once clicked or downloaded, they can give attackers access to your accounts or systems — or launch further attacks like ransomware.
Understanding what phishing scams are — and how they work — is the first step in defending against them.

What a Phishing Scam Looks Like (Now)
While some phishing attempts are still riddled with typos and poor grammar, many are now professionally written, often with the help of AI. But there are still tell-tale signs to look out for:
Phishing emails
Fake emails can be obvious at times, containing bad grammar and spelling mistakes but attackers are becoming smarter by using AI tools to create realistic looking email campaigns. There are still ways to check if an email is genuine or fake.
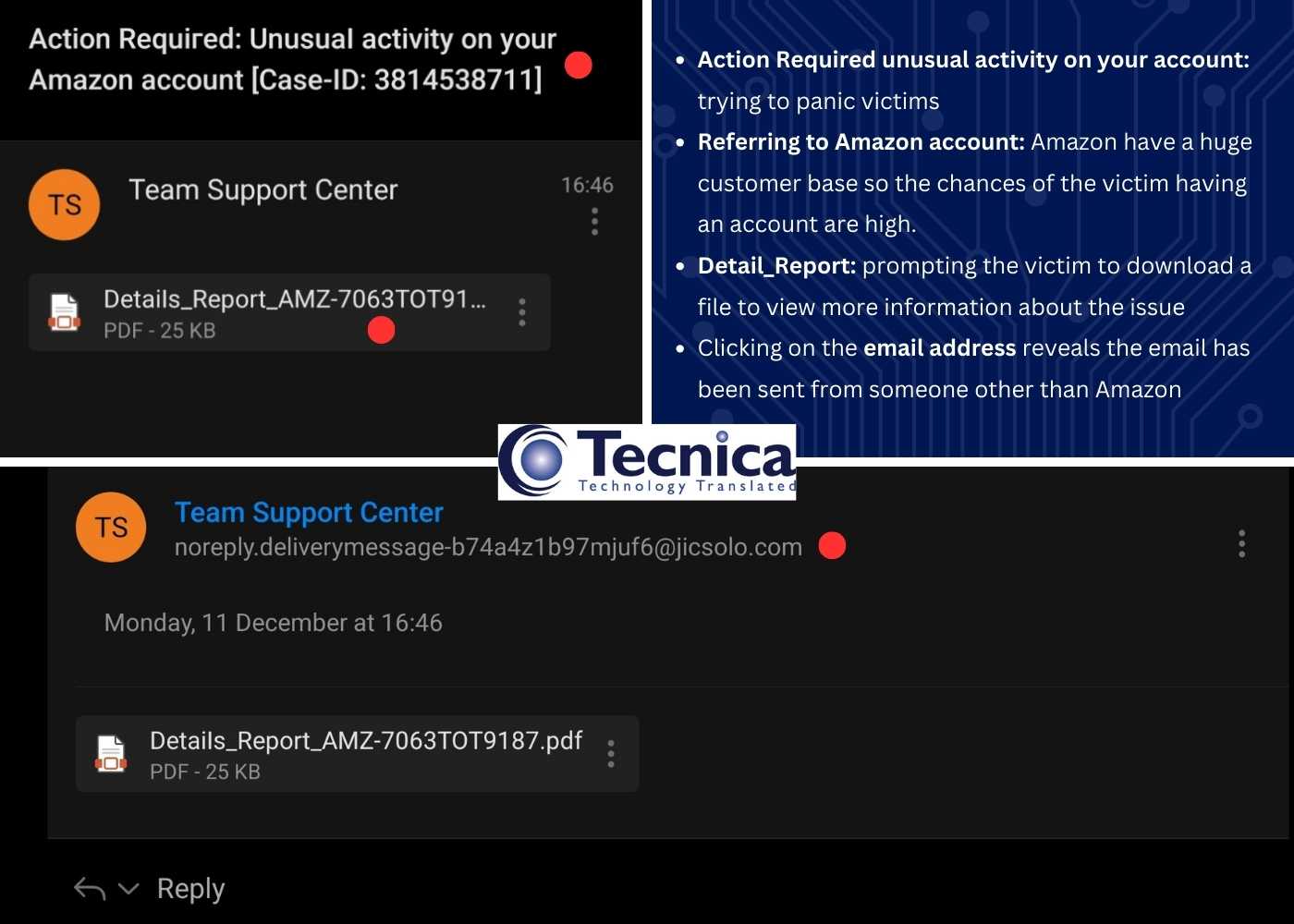
- Senders email address from a public email address like Hotmail.
- URLs contained within the email are misspelled e.g. www.amaz0n.co.uk/myaccount
- The email is asking for personal information like bank details, most reputable companies would not email and ask you to input banking information. If in doubt go to the company’s website directly, not through the link on the email, and check your account.
- Emails will often say things like “account suspended” or “payment declined, click here to resolve”. Again, check your account directly on the company website, do not click on any links within the email. These types of emails are sent to panic people and catch them off guard.
- The email may ask you to download the attached file. Never download any files unless you know where they are coming from, and you are expecting them.
- Emails requesting payment from companies like PayPal will often not be personalised e.g. Dear [email address] or Dear User, companies like PayPal will also not send attachments for customers to download. If you’re suspicious about the content of the email then this can be checked by logging into your account via your device or web browser.
- Attackers will also use current events to target victims. The COVID pandemic saw an exponential rise in phishing scams with attackers sending victims fake emails and SMS messages pretending to be the NHS asking them to book a COVID vaccine.
- Christmas time often sees a rise in fake emails. For instance, delivery companies claiming they are unable to deliver a parcel or phone companies like Three or EE asking for more information regarding your recent contract. All in the hopes of catching someone who has legitimately used these companies recently and thinks the email may be genuine.
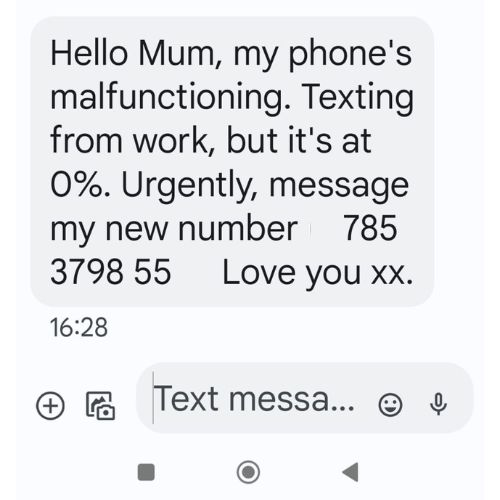
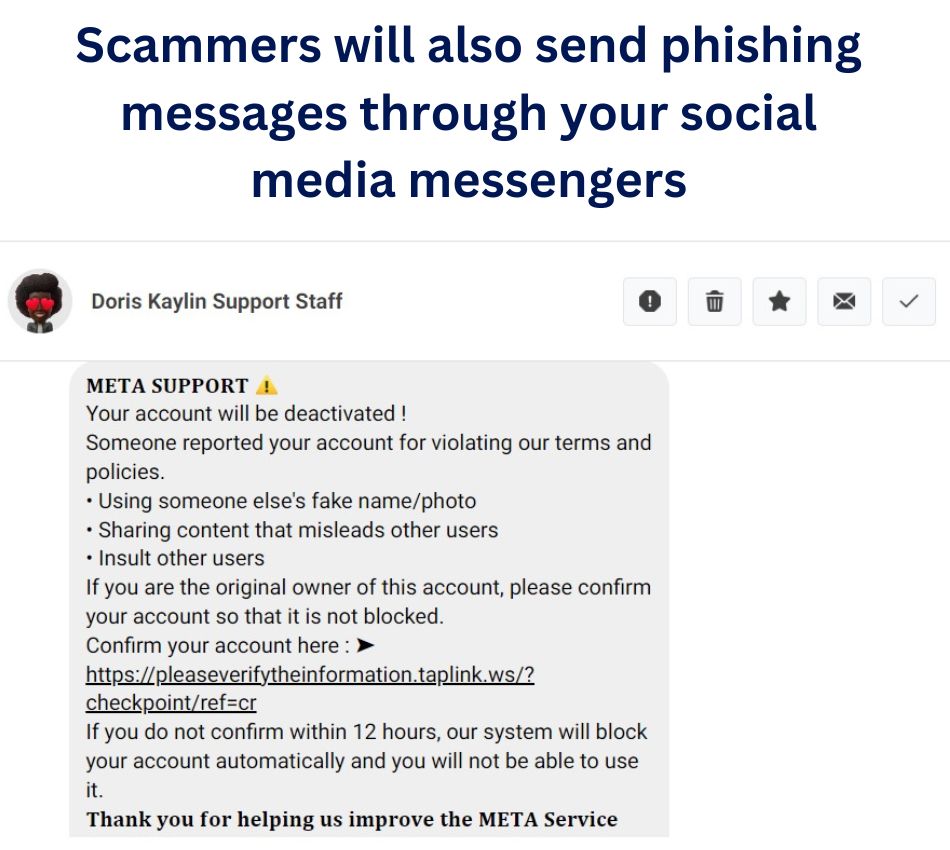
Phishing Texts and WhatsApp Messages
These are often short and urgent:
Messages saying you’ve won a prize — asking for bank details to “claim” it.
Message from an unknown number pretending to be a family member: “Hi Mum, I lost my phone…”
Claims of missed deliveries with links to pay postage fees.
The New Tactics: AI, Hybrid Work, and Supply Chain Risk
AI-Generated Phishing
Attackers are now using artificial intelligence to write convincing, error-free phishing emails that mirror corporate styles or even your own past communications. It’s getting harder to tell the difference.
Hybrid Work Vulnerabilities
With staff working across personal and business devices, often outside of secured office networks, attackers are exploiting weaker security environments and more informal communication channels.
Supply Chain Exploitation
Some phishing attacks now come through third-party suppliers or partners. A trusted vendor could unknowingly send a malicious file or link — giving attackers a way into your environment via the back door.
What Happens After the Click?
Often, phishing is just the first step. Once attackers gain access, they may deploy ransomware, locking files and demanding payment to release them. Increasingly, these attacks involve double extortion — where the data is also stolen and threatened with exposure.
Even worse? Some businesses still choose to pay. But paying the ransom fuels more attacks — and there’s no guarantee you’ll regain access or avoid public data leaks.
Why Phishing Keeps Working: The Cyber Security Skills Gap
There’s a shortage of cyber security professionals, leaving many organisations under-resourced and slow to respond to threats. Without expert insight, phishing scams slip through the cracks — especially when attackers are using real-time tactics to bypass traditional filters.
How to Protect Yourself and Your Business
It starts with awareness — and action:
- Never click on suspicious links or attachments — even if they appear genuine.
- Verify by going to the company’s website directly, not via the email or message.
- Use strong, unique passwords, and consider a password manager.
- Enable two-factor authentication (2FA/MFA – Multifactor Authentication) wherever possible.
- Keep devices and software updated, with antivirus and firewall protection in place.
- Back up your data frequently and store backups securely offsite.
- Report anything suspicious to your IT provider or internal team.
If you think you’ve been caught in a phishing scam
Contact Police Scotland if you think you have been scammed or think you may be a victim of fraud and you have lost money as a result.
For more information, please visit https://www.gov.uk/report-suspicious-emails-websites-phishing.
How Tecnica Helps Businesses Stay Secure and Resilient
At Tecnica, we provide expert support to help organisations defend against phishing and broader cyber threats. Whether you’re a small team or a large enterprise, we’ll work with you to strengthen your defences and recover quickly from attacks.
Our services include:
- Email and web filtering to block threats before they reach your inbox
- Endpoint and network security
- Business Continuity and Disaster Recovery (BCDR) — so you’re prepared if the worst happens
- Threat detection and response to act fast when an attack begins
We’re often called in when other IT providers are stuck — and our team has the knowledge and experience to get things back on track.
Be a Resilient Organisation
Cyber threats are evolving, but so can your defences. Tecnica helps you detect, respond and recover — with practical solutions and expert advice.
Cyber Security. BCDR. Resilience. Get in touch with Tecnica today.
We Recommend:
- Cyber Security
- Beware of Fake Job Scams
- Why an Email Security Policy Matters at Work
- Future Threats to Business Continuity for Scottish Businesses | BCDR Insights
- How Stronger Cyber Security Can Protect Your Business From Data Breaches
- Strengthening Your Business Security with SD-WAN


